A 1-Page Guide to Choosing a Meeting Recorder for High-Stakes Workflows
This checklist is for operational decision-making, not legal advice.
Use it to assess whether a meeting recording workflow is defensible by design, not just convenient.
Step 1 — Define the Sensitivity of the Conversation
☐ Does the meeting involve any of the following?
- Legal strategy, privileged communications, or case preparation
- Healthcare discussions involving PHI / ePHI
- Financial information, MNPI, or forward-looking disclosures
- Executive, board, HR, or internal investigation discussions
- Clients or stakeholders operating under GDPR or other strict privacy regimes
If YES, proceed with heightened scrutiny.
If NO, standard productivity tools may be sufficient.
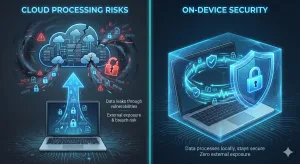
Step 2 — Identify Where Processing Must Not Occur
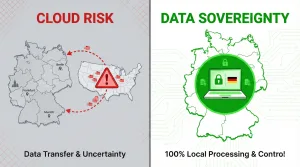
☐ Policy Decision — Cloud Processing Risk Posture:
- ☐ We accept cloud processing risks (Standard)
- ☐ We accept cloud processing only with signed BAAs / contracts and verified controls (Controlled)
- ☐ We categorically exclude cloud processing for this data (Strict)
☐ Do you know exactly where transcription and summarization occur?
- ☐ On your device
- ☐ In vendor-controlled cloud infrastructure
- ☐ Unclear / not fully documented
If the answer is unclear, assume risk exists.
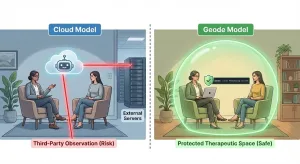
Step 3 — Map the Trust Boundary
☐ Who must be trusted for this workflow to remain confidential?
- ☐ Only the individual professional
- ☐ Internal IT / admin teams
- ☐ External vendors and subprocessors
- ☐ Policies, permissions, and correct configuration
The more parties involved, the more fragile the confidentiality model becomes.
Step 4 — Assess Compliance Reality (Not Claims)
☐ If regulated, do you have enforceable artifacts, not just assurances?
- ☐ Signed BAA (HIPAA contexts)
- ☐ Clear processor/subprocessor documentation (GDPR contexts)
- ☐ Documented access controls and auditability
- ☐ Defensible encryption and key-management model
Marketing statements do not substitute for enforceable controls.
Step 5 — Test Operational Behavior
☐ In real use, does the tool introduce any of the following?
- ☐ Bots or automated participants joining meetings
- ☐ Third-party or platform-controlled recording indicators that alter participant behavior
- ☐ Default sharing, syncing, or retention you must actively disable
- ☐ “Opt-out” settings that do not change underlying data flow
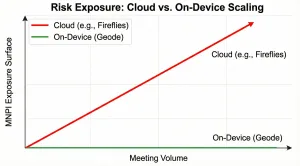
If controls rely on constant vigilance, risk compounds over time.
Step 6 — Consider Professional Etiquette & Trust
☐ Would the recording method feel appropriate if fully disclosed?
- ☐ To a client
- ☐ To a patient
- ☐ To opposing counsel
- ☐ To regulators or auditors reviewing the workflow later
Defensibility includes how the workflow appears, not just how it functions.
Decision Rule — Choose What Eliminates the Most Risk
Ask one final question:
Does this tool require me to manage confidentiality risk —
or does its architecture eliminate entire categories of risk by design?
- Managing risk requires policies, contracts, vigilance, and perfect execution
- Eliminating risk relies on structural constraints: where processing can occur
Choose the architecture that aligns with your worst-case scenario, not your best intentions.
Outcome
☐ Acceptable for high-stakes workflows
☐ Acceptable only for limited / low-sensitivity use
☐ Not defensible for our risk profile
Defensibility is not about convenience.
It is about fewer assumptions, fewer dependencies, and fewer things that can quietly fail.
© 2024 Geode Privacy Research. This framework aligns with GDPR & HIPAA architectural principles. Automate this workflow with Geode