This article is for operational clarity, not legal advice. If you handle PHI/ePHI, have counsel or your compliance lead review any vendor’s BAA and security posture before deployment.
Many healthcare and legal teams begin their evaluation by asking whether Otter.ai HIPAA compliant claims are sufficient for real-world use. But in HIPAA-sensitive environments, the more important question is rarely just “Is Otter.ai HIPAA compliant?”—it is whether the architecture and contracts together create a defensible workflow for HIPAA meeting recording.
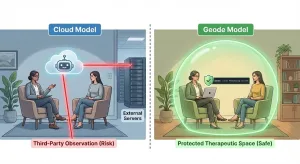
Otter.ai and similar AI meeting assistants can be useful. But for legal/medical secure transcription, surface-level compliance statements often hide deeper architectural assumptions about trust, access, and exposure.
That architectural framing matters because tools that look similar on the surface can impose very different risk profiles underneath. We explore that broader distinction in [Otter.ai vs Geode: Why Architecture Matters When Choosing an Otter Alternative], which examines how cloud-based and on-device models diverge in where data is processed, who must be trusted, and how exposure scales over time.
Below are three architecture preconditions you can use to evaluate whether a cloud speech-to-text workflow is appropriate in a HIPAA context—using Otter.ai as the reference case. This analysis avoids compliance accusations and focuses only on what can be verified.
Precondition 1: A BAA must exist before PHI touches the system
If your meetings may include PHI and the vendor will create, receive, maintain, or transmit that PHI on your behalf, HIPAA generally treats the vendor as a Business Associate. That typically means a Business Associate Agreement (BAA) must be in place before any HIPAA meeting recording occurs.
Why this is architectural (not political):
A cloud-based transcription service necessarily involves an external system handling ePHI. At that point, intent is not the control. The control is whether a signed BAA exists and whether it explicitly covers the services you plan to use.
What to check (practical):
- Does the vendor offer a BAA for your plan or tier, and will they sign it for your entity type?
- Does the BAA clearly define permitted uses, breach notification, subcontractors, and data destruction?
- Is your actual workflow—recording, transcription, summarization, storage, sharing—explicitly within scope?
Otter-specific note (factual framing):
Otter states publicly that it has achieved HIPAA compliance and references offering a BAA. For teams searching whether Otter.ai HIPAA compliant status is sufficient, treat this as a starting point—not the end. The enforceable control is your executed HIPAA BAA transcription agreement plus your configured workflow.
Lawyer-friendly line you can quote:
“HIPAA readiness starts with architecture plus contract: policy claims are not a substitute for an executed BAA.”
Precondition 2: You must understand the access surface (who can reach the data, technically)
In HIPAA work, “Who can access the data?” is not a marketing question. It is an ePHI access control question.
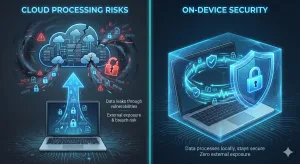
Cloud processing expands the access surface by design:
- Data transits networks.
- Data exists in provider-controlled environments.
- Administrative and operational systems may have access, depending on controls and contracts.
OCR guidance repeatedly emphasizes understanding the cloud environment, conducting risk analysis, and implementing appropriate safeguards.
What to check (practical):
- Are there admin or support access paths?
- Are role-based access controls, audit logs, and SSO enforced?
- What happens when links are shared or workspace settings change?
Architecture-enforced vs policy-based access:
- Policy-based access: “Access is controlled by permissions we promise to manage.”
- Architecture-based access: “Access is minimized because processing occurs in an environment you control.”
For teams evaluating legal/medical secure transcription, this distinction matters more than feature lists.
Cloud tools can be HIPAA-appropriate—but only if the access surface is fully mapped, audited, and constrained.
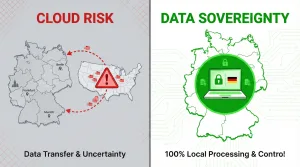
For a deeper look at how local processing eliminates this access surface entirely, see Cloud vs. On-Device Architecture.
Lawyer-friendly line you can quote:
“Architecture-enforced access beats policy-based access when confidentiality is the primary constraint.”
Precondition 3: Encryption and key management must match your risk tolerance
Many teams stop at “it’s encrypted.” HIPAA analysis usually needs one level deeper: Who controls the keys, and what happens during incidents?
OCR guidance highlights models where providers store encrypted ePHI but responsibilities remain shared.
What to check (practical):
- Encryption in transit and at rest.
- Whether “no-view” options exist—and what they mean operationally.
- Where keys live and who can access them.
- Data lifecycle controls, including deletion and termination handling.
Why this matters for healthcare and legal teams:
HIPAA does not forbid cloud processing. But it requires defensible safeguards—not assumptions.
For some organizations, this leads to evaluating on-device transcription for healthcare, where ePHI never leaves the local system and access is structurally constrained.
Lawyer-friendly line you can quote:
“Security posture is not a badge; it is the sum of key custody, access paths, and enforceable obligations.”
Instead of asking “Is Otter HIPAA compliant?”, ask:
- Will PHI be present?
- Will any part of that data be processed outside your controlled environment?
- If yes, do you have a signed BAA, verified ePHI access control, and a defensible key-management story?
If all three are satisfied, a cloud workflow may be acceptable.
If not, redesign the workflow so confidentiality is constrained by architecture—not promises.
[Download Geode for Mac] to explore on-device transcription for healthcare and confidentiality-sensitive professional work.