This article is written for operational clarity, not legal or regulatory advice. Financial institutions should review workflow and technology decisions with their compliance, risk, and information security leadership.
In financial organizations, meeting recordings are rarely “just notes.”
They often contain:
• Material non-public information (MNPI)
• Investment theses and allocation discussions
• Client portfolio details
• Internal risk assessments
• Pre-deal or pre-announcement conversations
As AI-powered meeting transcription tools become more common—including many cloud-based assistants often evaluated as a Fireflies alternative—financial teams adopt them for efficiency, sometimes without revisiting a more fundamental question:
What architectural risks are introduced when sensitive conversations are processed in the cloud, even when the tools themselves appear compliant and well-governed?
Below are four architecture-level risks that are frequently underestimated—not because teams are careless, but because these risks emerge from how systems are built, not from how features are marketed.
⸻
Architectural Risk 1: Data Gravity Accumulates Faster Than Governance Can React
Cloud-based meeting tools centralize value by design. But for firms focused on MNPI protection and data sovereignty, this centralization creates a compounding risk.
Each recorded meeting adds:
• More sensitive audio
• More derived text (transcripts, summaries, action items)
• More historical context linked to people, deals, and timelines
Over time, this creates data gravity:
the tendency for sensitive information to accumulate in one external system faster than governance controls evolve.
Even with strong policies in place, teams must continuously manage:
• Retention rules
• Access reviews
• Offboarding controls
• Incident response assumptions
This is not a failure of discipline—it is a structural property of centralized cloud systems.
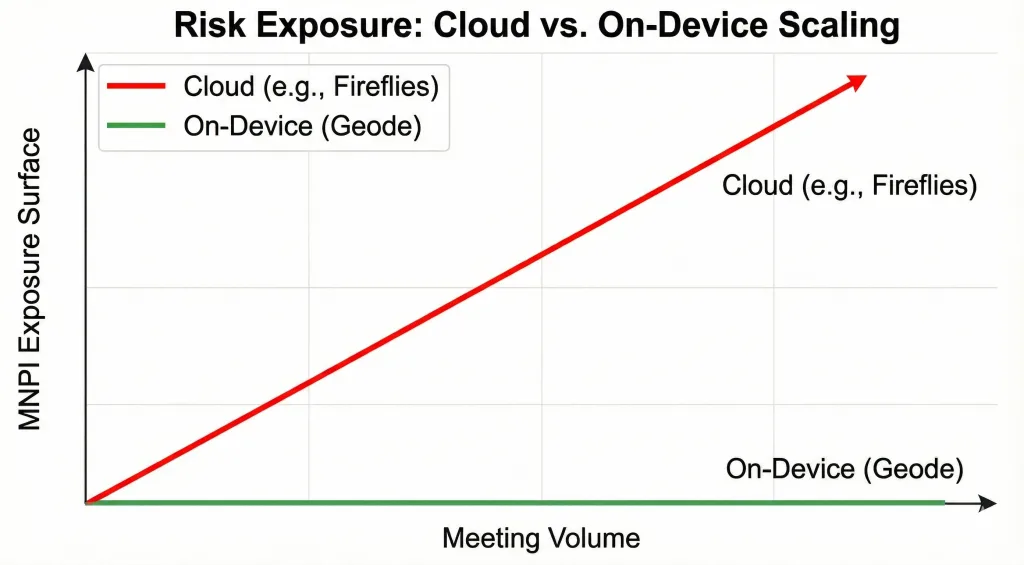
By contrast, architectures where transcription and summarization occur locally do not create a growing external data repository. Risk does not compound simply because usage increases—an important distinction for teams considering local AI meeting notes rather than centralized cloud archives.
⸻
Architectural Risk 2: Access Is Broader Than Most Threat Models Assume
Financial teams often ask, “Who can see our data?”
The more precise question is:
“Through how many technical paths could access occur?”
In cloud processing models, those paths may include:
• Administrative and support access
• Operational debugging workflows
• Account recovery mechanisms
• Enterprise admin consoles
• Subprocessor environments (depending on service design)
These paths may be:
• Logged
• Restricted
• Contractually governed
But they still exist.
This matters in finance, where financial meeting transcription risk is often underestimated because access paths are abstracted away behind vendor assurances.
Architectures that process data entirely on the user’s own hardware collapse this access surface by design. There is no external system in which access must be modeled, audited, or justified.
For teams evaluating on-device meeting transcription for financial services, this structural containment often outweighs the collaboration benefits of cloud-based tools positioned as a Fireflies alternative.
For a detailed, side-by-side breakdown of how cloud-based and on-device architectures differ in terms of data flow and access surfaces, see our
[Cloud AI vs On-Device AI: Two Fundamentally Different Architectures].
⸻
Architectural Risk 3: Configuration Controls Are Fragile Under Time Pressure
Cloud tools rely heavily on configuration:
• Permissions
• Workspace rules
• Sharing defaults
• Admin settings
• Feature toggles
In calm environments, these controls work well.
In financial contexts, however, time pressure is the norm:
• Market volatility
• Live deal negotiations
• Crisis response
• Regulatory deadlines
Under pressure, configuration errors become more likely—not due to negligence, but due to operational reality.
Architecture-level constraints behave differently.
If sensitive processing cannot leave the device:
• There is nothing to misconfigure
• There is no sharing default to forget to disable
• There is no backend setting to audit after the fact
This distinction—configuration vs. structural constraint—is central to understanding real-world cloud-based meeting recording risk.
⸻
Architectural Risk 4: Compliance Narratives Lag Behind Technical Reality
Financial organizations often rely on compliance narratives:
• “We have a vendor assessment.”
• “We reviewed the SOC report.”
• “We configured access correctly.”
• “We obtained the necessary assurances.”
These steps are necessary—but they are not the same as architectural containment.
Regulators and auditors increasingly ask not just whether controls exist, but how risk is constrained when controls fail. In an era of heightened scrutiny on off-channel communications and data residency, reliance on vendor promises is becoming a harder position to defend—particularly in light of SEC enforcement actions related to recordkeeping and unmonitored communications.
Just as personal messaging apps have created compliance blind spots, cloud-based AI meeting tools—even those marketed as a Fireflies alternative—can introduce similar exposure if MNPI meeting notes security is not enforced by architecture.
Cloud-based tools assume:
Controls + policies + contracts = acceptable risk
On-device architectures assume:
Risk is constrained by where computation is physically possible
Neither model is universally “right.”
But they lead to very different failure modes—and different questions during audits, investigations, or post-incident reviews.
⸻
When Cloud-Based Meeting Tools Make Sense in Finance
Cloud architectures are often appropriate when:
• Collaboration across large, distributed teams is essential
• Information is intended to be broadly shared
• Governance frameworks are mature and continuously enforced
• Centralized oversight is a requirement, not a liability
Many financial workflows fall into this category.
The key is intentional alignment—not default adoption.
⸻
When Financial Teams Reconsider Cloud Processing
Some financial teams intentionally avoid cloud-based meeting processing for:
• Investment committee discussions
• Pre-trade or pre-announcement conversations
• Client strategy reviews
• Internal risk or stress-test meetings
In these scenarios, teams often prefer architectures where:
• Transcription and summaries are generated locally
• Sensitive content never enters an external processing pipeline
• Risk does not scale simply because usage increases
This is an architectural decision—not a feature comparison.
⸻
The Takeaway: Architecture Determines the Shape of Risk
The most overlooked risks in financial meeting transcription are not bugs or breaches.
They are structural:
• Where data accumulates
• How access paths multiply
• How configuration errors emerge under pressure
• How governance narratives diverge from technical reality
Understanding these dynamics allows financial teams to choose tools—and architectures—that match their actual risk tolerance, not just their productivity goals.
⸻
A quiet next step
If your team is evaluating how to capture meeting notes without expanding external exposure, it may be useful to examine how fully on-device approaches constrain risk by design.
[Download Geode for Mac] to explore on-device meeting transcription and summaries — designed to keep MNPI within your firewall.